In a digital landscape like 2024, phishing attacks have become increasingly sophisticated, costing businesses and individuals billions annually. This comprehensive guide explores the latest phishing threats, from AI-powered scams to advanced social engineering tactics, offering expert insights on protecting yourself and your organization.
Whether you’re a cybersecurity professional, business owner, or concerned individual, you’ll discover actionable strategies to identify, prevent, and respond to phishing attempts. With cyber threats evolving daily and a reported 90% of data breaches starting with a phishing email, understanding these attacks has never been more crucial.
In this article, discover how to safeguard your sensitive information from the latest phishing tactics, including business email compromise (BEC), smishing, and deepfake-based attacks. We cover everything you need—from identifying threats to learning effective protection strategies.
What is phishing?
Phishing is the attempt to obtain sensitive information such as usernames, passwords, banking records or account numbers, social security numbers, and financial information, by replying to the email, social media message or entering it on a website.
Today, phishing, a term associated with email fraud, has emerged as one of the most common types of cyberattacks. Phishers can pretend to represent a legitimate bank, organization, government agency, or store, or claim to be the host of a lottery or contest.
Although spam mail filters and security processes reduce the threat to our emails, they cannot eradicate all phishing. The best way to avoid becoming a phishing scam victim is to not fall for it.
Why This Article Matters: 2024 Updated Statistics
Recent data shows an alarming increase in phishing threats:
- In 2023, 90% of organizations worldwide experienced at least one successful phishing attack
- Business Email Compromise (BEC) attacks caused average losses of $125,000 per incident in 2023
- Mobile phishing attacks increased by 50% in 2023 compared to 2022
- 1 in 99 emails is now a phishing attempt
- AI-generated phishing emails have increased by 1,264% since 2022
- 84% of organizations experienced a successful phishing attack that got past their security defenses
- Smishing (SMS phishing) attacks increased by 700% in the first half of 2023
*Stats from FBI Internet Crime Report 2023 | Proofpoint’s 2024 State of Phishing Report | Verizon’s 2023 Data Breach Investigations Report | CheckPoint Research 2023
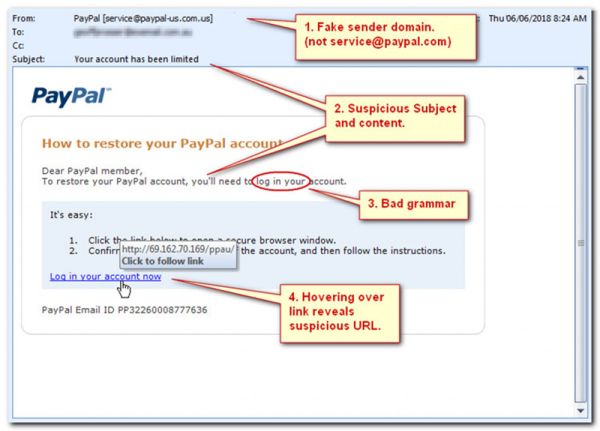
How to Spot a Phishing Email
While successful phishing messages are increasingly sophisticated, especially with AI-generated content, several modern indicators can help identify a phishing attempt. Usually, they are represented as being from a well-known company, including corporate logos and other collected identifying data.
- Identify the Sender. Is this person someone you know? Did you expect an e-mail from them or does this correspond to your work role? If not, it is probably suspicious.
- Email subject: Using poor grammar and punctuation usage, suspicious subject.
- Reply-to. If the Reply-to address is different from the sending address, this should raise your suspicion for the whole message.
New red flags to watch for:
- OAuth Phishing: Attackers request app permissions instead of direct credentials
- Conference/Meeting Invites: Fake virtual meeting links leading to credential theft
- Document Share Notifications: Impersonating SharePoint, Google Docs, or OneDrive
- Modified Characters: Using similar-looking characters (like raýpal.com instead of paypal.com)
- AI Detection: Watch for inconsistent writing styles or unusual word choices that might indicate AI-generated content
- Subscription Cancellations: Fake Netflix/Spotify cancellation emails
- Package Delivery: Updated shipping scams (links or QR codes)
- Cloud Storage: Fake storage quota warnings
- Software Updates: Fake security update notifications
- QR code phishing with malicious QR codes leads to fake login pages
Other red flags
- Links
Don’t open attachments or links you didn’t expect, and if you don’t know the sender, don’t answer the call, otherwise, report it. Links may take you to bogus websites or cause your computer to download dangerous files. To check that the address matches the input link, you can hover the cursor over it before clicking. The fraud is achieved by “masking” a malicious link through a link-shortening service such as Bitly, or any other popular services. Bad actors will use shortened URLs to direct victims to phishing sites or initiate a download of malicious software onto your device.
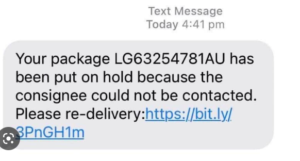
If you are suspicious of a shortened URL, don’t click it.
There are a few ways you can reveal the full URL behind a shortened URL:
- Use the shortening service preview feature. Type the shortened URL in the address bar of your web browser and add the characters described below to see a preview of the full URL:
- tinyurl.com: Between the “http://” and the “tinyurl”, type preview
Example: http://preview.tinyurl.com/zn7xnzu
-
- bit.ly: At the end of the URL, type a +
Example: http://bit.ly/2DuNkeV+
- Use a URL checker. These are a few of the sites that allow you to enter a short URL and view the full URL:
Other clear warning signs:
- Attachments
To make sure the title of an attachment matches the file type, hover over it. It’s possible that a file with the name “something.exe” is what appears to be a document with the name “something.pdf.” The attachment is essentially a software application that you execute if it has an a.exe extension, making it incredibly dangerous and capable of infecting your device and erasing your data.
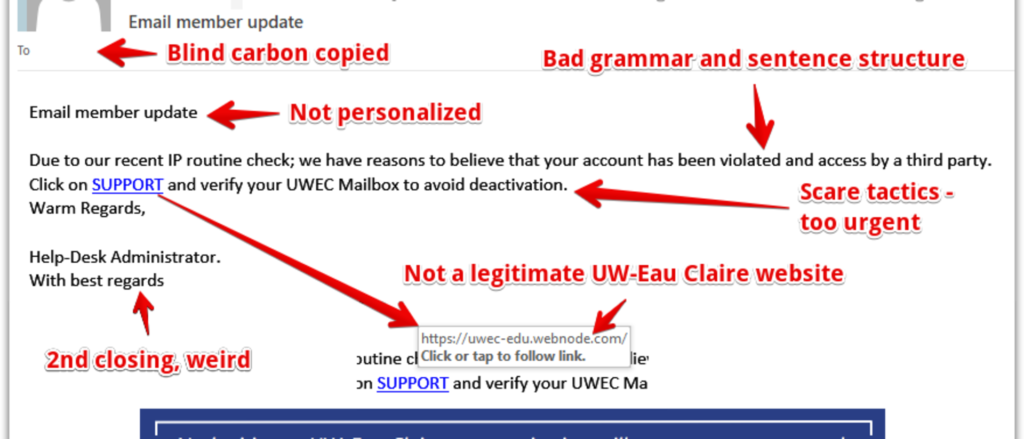
Urgency
Phishing attacks attempt to induce panic in the receiver and cause the person to act before investigating the authenticity of the request. Unusually short deadlines create a false sense of urgency to act. Attackers employ this technique in attempts to confuse the recipient.
- Grammar
Phishing messages are notorious for containing misspelled words or poor grammar starting from the subject line and continuing to the email content and signature.
- Emotions: Be wary of any e-mails trying to cause certain emotions. The most commonly used malicious emotions are:
- Greed: Messages offering or promising you money by clicking a link. If it seems too good to be true, it probably is 😬.
- Curiosity: Attackers take advantage of our curiosity by promising something exciting or prohibited content.
- Fear: Threatening recipients with negative consequences is a common tactic to generate responses—things such as threatening to shut off accounts or legal action
How is phishing harmful?
The obvious:
- Steals your login credentials (self-explanatory, right?)
- Someone can now impersonate you
- Someone could steal your identity
- Installs Malware (talk specifically about key loggers, screen watchers, other MITM (man-in-the-middle) software, etc.)
- Malicious sites navigated to in a phishing attempt sometimes
- Install malware on client machines.
- Encourage you to take fraudulent action/s (social engineering aspect)
- Initiate and/or approve illegitimate financial transactions
- Send sensitive information to unauthorized parties
The not-so-obvious:
- With your credentials, attackers can gather metadata about you
- Metadata is super important
- Allows attacks on other sites
- Related attacks
- Credential stuffing: Using stolen credentials from one site in other sites (don’t reuse passwords across multiple sites). If your login details for one site (let’s say a social media account) are stolen, they can be used to try to get into other services (like a bank account).
- Crypto-jacking: Using your browser or computer to mine cryptocurrency
- Session Hijacking: Type of Man-in-the-Middle attack

Tips to avoid a phishing scam
To avoid falling victim to phishing scams, it’s important to stay vigilant for suspicious emails or text messages. Legitimate companies will never ask for personal information through email, so never share your personal or financial details in response to such requests, no matter how credible the sender appears.
Avoid clicking on links or attachments in suspicious messages; instead, use a search engine to find the legitimate website directly. If the web address from the search results doesn’t match the one in the email, it’s probably a phishing attempt and should be deleted. Setting up a spam filter can help reduce the number of phishing emails you receive. If you’re still tempted to click on a suspicious link, pick up the phone and contact the company directly, but don’t use any phone numbers provided in the email, as they could be fake.
It’s also wise to use a password manager and change your passwords regularly for added security, even if you haven’t encountered a suspicious email. Enabling Multi-Factor Authentication (MFA) wherever possible adds another layer of protection, and monitoring your accounts regularly can help detect any unusual activity early.
Final Recommendations
Phishing continues to evolve, but so do our defenses. Stay vigilant, stay informed, and maintain good security practices. The best defense is a combination of technology, awareness, and proper procedures.
Remember: the type of attack isn’t as important as the recognition of an attack. Always think before you click!

