Your bank account drained overnight. Your social media account hijacked. These aren’t just horror stories—they’re the daily reality for thousands of people whose digital lives are shattered by cybercriminals. In 2024 alone, cybercrime has evolved from simple email scams to sophisticated AI-powered attacks that can mimic your voice, clone your digital identity, and breach even seemingly secure systems.
But here’s the good news: you don’t need to be a tech expert to protect yourself. While cybercriminals are growing bolder, the most devastating attacks often succeed because of basic security oversights that anyone can fix. In this guide, we’ll cut through the techno-jargon and share five battle-tested strategies that can shield your digital life from today’s most dangerous cyber threats.
1. Stay Cautious: Verify Emails, Calls, and Messages
Phishing is a major cyber threat where scammers pose as banks, services, or colleagues to steal sensitive information. Stay vigilant to avoid falling victim.
Example #1
You receive an email from your “bank” about suspicious account activity, urging you to click a link and log in. The site looks real—but it’s a scam.
How to Protect Yourself:
- Check the sender’s email for misspellings or unusual domains.
- Hover over links to preview suspicious URLs before clicking.
- Call your bank using their official number to verify the request.
By taking these precautions, you can prevent phishing attacks and keep your data secure.
Example #2
Imagine receiving an email that looks like it’s from Booking.com, offering a €150 gift.
At first glance, it seems like a great deal—but a closer look at the sender’s email address reveals something suspicious. Instead of coming from @booking.com, the email is sent from @etu.univ-savoie.fr, which belongs to an academic institution, not Booking.com.
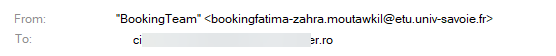
This mismatch is a red flag. Legitimate companies always send official communications from their own domain. If an email claiming to be from Booking.com isn’t using an @booking.com address, it’s likely a phishing attempt.
Whenever you receive an unexpected email offering rewards or gifts, always verify the sender’s email address. Scammers often use lookalike domains to appear legitimate, but small inconsistencies—like a mismatched domain—can help you spot fraud and avoid phishing scams.
Spotting Red Flags: How to Identify Phishing Emails Masquerading as Legitimate Offers
In addition to checking the sender’s email, there are several other red flags in this message that suggest it might be a phishing attempt:
- Spelling and Grammar Errors:
- The email subject and content contain multiple small errors, such as “Your Booking gif234546” (instead of “gift”) and the awkward phrasing “for their loyalty to our program.” Professional companies like Booking.com typically use proper grammar and spelling in official communications.
- Unusual Urgency and Call to Action:
- The email urges you to “Claim Now” and emphasizes that this offer expires before a certain date. Phishing emails often create a sense of urgency to prompt quick action without thinking.
- Generic Language:
- The email lacks personalization. Legitimate companies often address customers by name and refer to specific booking details or loyalty information. Here, it’s simply “our customer,” which is a common tactic in phishing emails to target many people with a single message.
- Generic “Gift Card” Offer:
- The email offers a “gift card,” a common phishing lure. Booking.com typically doesn’t provide such rewards without clear communication or specific qualification criteria.
- Suspicious Link:
- Although we can’t see the actual URL in the “Claim Now” button, you could hover over the link (without clicking) to see if it leads to an official Booking.com page. Phishing emails often include links that appear legitimate but redirect to unrelated or suspicious sites. A genuine Booking.com link would have a secure https://www.booking.com
- Unusual Contact Information:
- The footer presents Booking.com’s address vaguely and without consistent formatting. Reputable companies provide clear, official contact details, including phone numbers and direct website links.
- Too Good to Be True Offer:
- A random 150 Euro gift without prior communication or reason is unusual, especially without any context or clear terms and conditions. Companies like Booking.com typically announce rewards transparently and in a context that makes sense (like after a promotion).
By cross-checking these elements, you can better avoid falling for scams like this one.
2. Update Passwords: Regularly Change Compromised Passwords and Avoid Reusing Them
Reusing passwords across multiple accounts is a major security risk. If just one account is compromised in a data breach, all linked accounts using the same credentials become vulnerable. Regularly updating your passwords and ensuring each one is unique helps protect your digital identity.
Example #4
Consider this scenario: you use the same password for both your email and social media. If a hacker breaches your social media account, they can use the same credentials to access your email—where they could reset passwords, access sensitive financial details, or even impersonate you.
To combat this:
- Use a password manager to generate and store unique, complex passwords for each account.
- Enable two-factor authentication (2FA) wherever possible to add an extra layer of security.
By making these changes, you reduce the chances of a widespread breach in case one of your accounts is compromised.
3. Use VPNs: Avoid Public WiFi, or Use a VPN When Necessary
Public WiFi networks in cafes, airports, and libraries lack proper security, making them a prime target for cybercriminals. They can intercept unencrypted data, exposing login credentials and payment details. A VPN (Virtual Private Network) encrypts your connection, ensuring your data stays protected even on public networks.
Example #5
You’re at a coffee shop and need to check your bank account. You connect to the public WiFi and log into your banking app. Without a VPN, your data is exposed, and a hacker on the same network could intercept your login details.
To protect yourself:
- Use a VPN whenever you’re connected to public WiFi to ensure that your data is encrypted and secure.
- If you can, avoid accessing sensitive accounts (like banking or personal email) on public networks altogether. Wait until you’re on a trusted, secure network, such as your home WiFi.
4. Freeze Your Credit: Prevent Identity Theft by Locking Your Credit
Freezing your credit is a highly effective method to prevent identity theft. It restricts creditors and financial institutions from approving loans, credit cards, or lines of credit in your name, particularly if your personal information has been compromised.
Example #6
If your Social Security number or personal data is exposed in a breach, a hacker could attempt to open accounts under your name. By freezing your credit with major credit bureaus, you block unauthorized access, preventing misuse of your information. You can easily unfreeze your credit when necessary, offering a flexible and secure solution for protecting your identity.
5. Be Careful With Personal Information: Post Minimally on Social Media
Oversharing on social media can make you an easy target for cybercriminals. Information like your birthday, location, and vacation plans can be exploited to answer security questions, impersonate you, or even break into your home while you’re away.
Instead:
- Limit the details you share online, such as your birthdate, home address, or travel plans.
- Adjust privacy settings on platforms like Facebook, Instagram, and LinkedIn to control who sees your posts.
- Be cautious about accepting friend requests or connections from strangers, as scammers may use fake profiles to collect information.
In today’s interconnected world, protecting your online identity is essential. By following these strategies—updating passwords, using VPNs on public networks, freezing your credit, and being mindful of what you share online—you can significantly reduce your exposure to cyber threats.
Own Your Digital Security: Stay One Step Ahead of Cyber Threats
Your online identity is a valuable asset—don’t leave it unprotected. With cybercriminals constantly finding new ways to exploit personal data, the best defense is a strong, proactive approach. Simple actions like updating passwords, using VPNs on public networks, freezing your credit, and being mindful of what you share online can drastically minimize your risk.
Hackers don’t take breaks, and neither should your cybersecurity habits. Staying informed and adopting these protective measures isn’t just about avoiding threats – it’s about taking control of your digital presence and ensuring peace of mind in an increasingly connected world. Remember, online security is an ongoing effort.
Start making cybersecurity a priority today! Take charge, stay vigilant, and protect what matters most – your digital identity.

