In today’s digital age, Personally Identifiable Information (PII) is often collected and stored by organizations, and it is important for us to understand the types of information that constitute PII, how it is collected, and how it is protected. In this article, we will explore what PII is, examples of PII, how it is collected, and steps you can take to protect your PII.
What is Personally Identifiable Information (PII)?
Personally Identifiable Information (PII) is any information that can be used to identify an individual. This can include a person’s full name, social security number, date of birth, address, phone number, email address, driver’s license number, passport number, and biometric data such as fingerprints and facial recognition. PII can also include sensitive information such as medical records, financial information, and employment records.
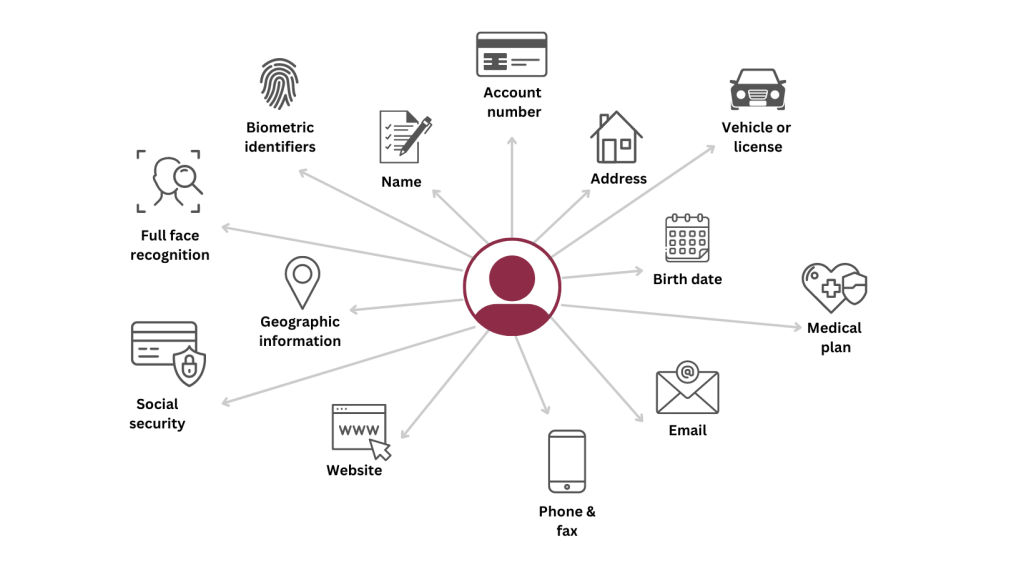 In addition to obvious identifiers, there are quasi-identifiers or pseudo-identifiers that, when combined with other data, can reveal a person’s identity. For instance, a US government study found that 87% of the US population could be uniquely identified by a combination of gender, ZIP code, and date of birth. While pseudo-identifiers may not qualify as Personally Identifiable Information (PII) under US law, they will likely be considered PII in Europe.
In addition to obvious identifiers, there are quasi-identifiers or pseudo-identifiers that, when combined with other data, can reveal a person’s identity. For instance, a US government study found that 87% of the US population could be uniquely identified by a combination of gender, ZIP code, and date of birth. While pseudo-identifiers may not qualify as Personally Identifiable Information (PII) under US law, they will likely be considered PII in Europe.
One example of quasi or pseudo-identifiers in the EU is IP addresses. While IP addresses are not always considered Personally Identifiable Information (PII) on their own, when combined with other data, they can be used to identify an individual.
For example, if an online retailer collects your IP address when you make a purchase, and then combines that with your name and address that you provided during checkout, they could use that information to track your online activity and target you with personalized advertising. In this case, the IP address would be considered a quasi or pseudo-identifier that, when combined with other information, can reveal your identity and be considered as PII.
Under the EU’s General Data Protection Regulation (GDPR), such personal data, including pseudo and quasi-identifiers, is subject to strict rules governing its collection, use, and protection.
Personally Identifiable Information (PII) in Privacy Law
Privacy laws in many countries and places have similar terms for Personally Identifiable Information. For example:
In the European Union, according to directive 95/46/EC “personal data” means information that can tell who someone is by an ID number or specific things about their physical, physiological, mental, economic, cultural, or social identity.
In the United States, PII is things like your name, social security number, or biometric records that can reveal who you are according to the National Institute of Standards and Technology (NIST)’s Guide to Protecting the Confidentiality of Personally Identifiable Information.
In Canada, “personal information” is data that can tell who someone is, either by itself or when combined with other information, according to Personal Information Protection and Electronic Documents Act (PIPEDA) and Privacy Act.
In Australia, the definition of “personal information” in the Privacy Act 1988 is wider than in many other places. It includes any information or viewpoint about someone, true or not, that can identify them or could be figured out by someone else.
In New Zealand, the Privacy Act defines “personal information” as any information about someone alive and can be identified via their name, health contact details, or financial records.
How is PII collected?
PII can be collected in several different ways. Here are some examples:
- Online forms: Many websites and apps require users to fill out online forms with personal information such as their name, address, and phone number.
- Social media: Social media platforms collect a wealth of personal information about users, including their names, ages, location, interests, and friends.
- Customer accounts: Many organizations require customers to create an account to use their services. This often involves providing personal information such as their name, address, and payment information.
- Credit checks: When applying for credit, individuals may be required to provide personal information such as their social security number, employment information, and income.
- Surveys: Organizations may conduct surveys to collect information about their customers, which may include personal information.
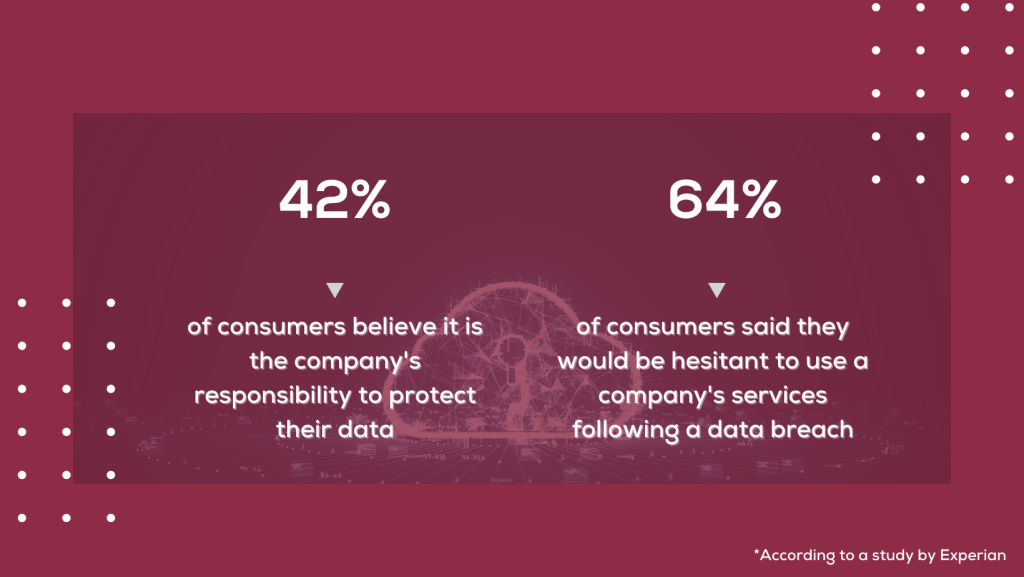
Who is responsible for safeguarding PII?
When it comes to protecting Personally Identifiable Information (PII) from a legal point of view, organizations may not be the only ones responsible for keeping it safe. The people who own the data may also have some responsibility. While companies may or may not be legally liable for the PII they possess, public perception largely places the responsibility on these organizations.
Establishing a Framework for Data Privacy
As such, securing PII is a widely accepted best practice, which can be achieved by implementing a Data Privacy Framework.
A documented conceptual structure known as a Data Privacy Framework assists businesses in safeguarding sensitive data, including personal information, payments, and intellectual property. This framework shows how to identify important information, assess risks that could affect it, and use measures to keep it safe. There are some frameworks already made for data privacy, such as the EU General Data Protection Regulation (GDPR), the ISO 27000 family of standards, and the Payment Card Industry Data Security Standard (PCI DSS). Your organization’s Data Privacy Framework enables more protection and lets you focus on the most crucial information and design safeguards that work with your organization’s style, rules, laws, and budget.
Steps to establishing a personalized Data Privacy Framework in your organization
- Classification
To classify PII, an organization should first identify, evaluate, and categorize the information it receives, stores, manages, or shares. For each type of PII, the organization should determine the necessary level of confidentiality, how vital it is to maintain the accuracy and completeness of the data, how crucial it is to have the data accessible at all times, and what kind of consent the organization has obtained regarding the information.
- Assessment
To evaluate the risks of each type or category of PII, an organization should perform a Privacy Impact Assessment (PIA). The PIA should analyze how the PII is collected, stored, and discarded, as well as the possible security risks for each type of PII.
- Compliance Environment
Regarding compliance with PII, an organization should establish a Compliance Environment that outlines its legal responsibilities in the territories where it operates, identify voluntary standards to adhere to, and establish security and liability policies for third-party products and services (like payment processors, cloud storage, website analytics tools, email marketing platforms, etc).
- PII Security Controls
To prevent data loss or leaks, an organization should specify which PII security controls it must implement. These controls may involve change management, data loss prevention, data masking, ethical walls, privileged user monitoring, sensitive data access auditing, secure audit trail archiving, user rights management, and user tracking.
Steps to protect PII
Individuals need to take steps to protect their PII. Here are some best practices:
- Be cautious with your personal information: only provide personal information when it is necessary and only to trusted sources.
- Use strong passwords: use unique, strong passwords for all of your online accounts, and use a password manager to keep track of them.
- Secure your devices: keep your devices up to date with the latest security patches, and use antivirus software to protect against malware.
- Be mindful of phishing scams: phishing scams are designed to trick individuals into giving away their personal information. Be wary of emails, phone calls, or text messages that ask for personal information.
- Use two-factor authentication: two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring a second form of verification, such as a code sent to your phone or email.
Final thoughts
Personally Identifiable Information (PII) is a critical concern in today’s digital age. Understanding what PII is, how it is collected, and how to protect it is essential for all of us, individuals and organizations. By taking steps to safeguard our PII, we can help to reduce the risk of identity theft, financial fraud, and other types of cybercrime.
Start building trust with your customers today! Safeguard their data and gain a competitive advantage with Ropardo’s software solutions. Contact us and learn how we can help enhance your customer experience while protecting their privacy.